scotty85
Extreme Android User
with the rezound,some folks unknowingly re-unlocked after s off to regain use of fastbooot commands,after running ruus that replaced the patched jpbear hboot. i thot i would bring this here,in case there ever becomes a need.
i happened across this thread inthe gsm evo 3d forum: http://forum.xda-developers.com/showthread.php?t=1970252 and found it to work on the rezound,inc 4g,sensation 4g,cdma evo 3d,MT4GS,Amaze 4g,and prolly several others.
this does NOT mean you can unlock your bootloader without going thru htcdev. all this means,is that if you accidentally unlocked your bootloader after s-off,you can get rid of the relocked watermark and get back to 100% locked prior to s-on for warranty purposes,without having to s-on and re-s off.
ive always been unlocked. for S&Gs,i dumped mmcblk0p3 and found the described "HTCU" at 0x8404. changed it to 0x00000000 and voila! back to locked
afterward,relfashed my origianl mmcblk0p3,wich brought me back to unlocked with no getting or flashing tokens.
this is NOT a patched or hex edited hboot.again,this is ONLY to get back your original ***locked*** status.
*this is for s-off phones only
2 ways to do it:
1)old school
this assumes you to have drivers,adb/fastboot,a hex editor,a fair understanding about what youre doing,and the ability to follow directions on the linked thread
2)noob friendly
-download the appropriate zips,place on sd card.
-boot to recoverywipe cache/dalvik
-flash in recovery. i recomend to run query first,to make sure its working. tested on my personal amaze,jetstream,rezound,inc 4g,sensation,MT4GS,and gsm evo 3d.
query:query_bootloader.zip
query_bootloader.zip f335f78f9f46469c823da0c671026de5
unlock:unlock_bootloader.zip
unlock_bootloader.zip f335f78f9f46469c823da0c671026de5
lock:lock_bootloader.zip
lock_bootloader.zip f335f78f9f46469c823da0c671026de5
a little bit of explanation. yes,the md5s are all the same. its the same file,just named differently. the script behaves based on the name of the zip. i knew if i only included 1 download and instructed folks to change the name there would be confusion,so this is my attempt to keep it simple. feel free to download one file and just change the name to make the other zips.
it also works to make your phone relocked if for some reason you want it that way(rename relock_bootloader.zip). i didnt include a zip for that because i figued there would be no demand.
before:
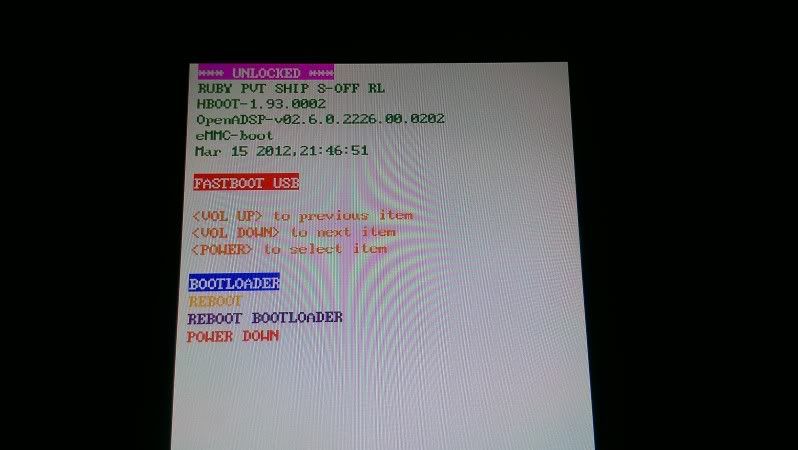
after:
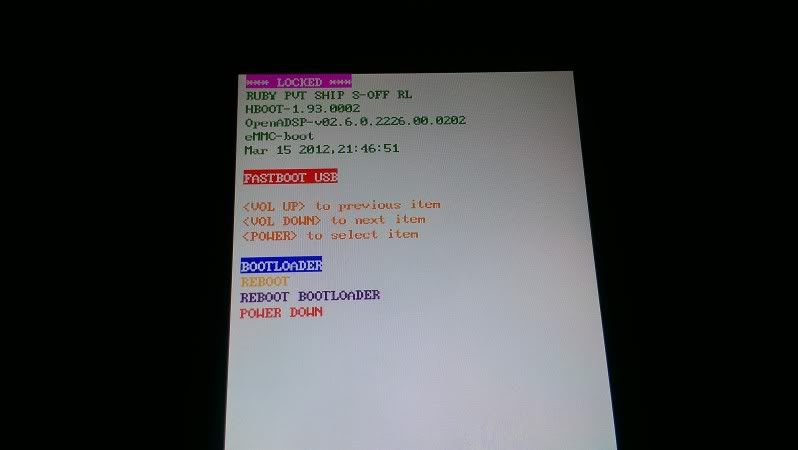
sure,i could have easily faked the above photos,but i dint.
again,all credit goes to s trace on the above thread,be sure to click the thanks button on his post. all i did was remove the device check per his instruction. DO NOT flash on other devices without checking for the proper location of the lock flag first.
DISCLAIMER:this is not my work. i have tested it on my own device,but use it at your own risk. if it melts your phone into a lil pile of goo,its not my fault.
enjoy
special thanks
-brian for unlocking his bootloader,then dumping mmcblock0p3 to make sure it would work for cdma evo3d phones too
-brian and donb for fearless testing of the zip files on evo3d cdma
i happened across this thread inthe gsm evo 3d forum: http://forum.xda-developers.com/showthread.php?t=1970252 and found it to work on the rezound,inc 4g,sensation 4g,cdma evo 3d,MT4GS,Amaze 4g,and prolly several others.
this does NOT mean you can unlock your bootloader without going thru htcdev. all this means,is that if you accidentally unlocked your bootloader after s-off,you can get rid of the relocked watermark and get back to 100% locked prior to s-on for warranty purposes,without having to s-on and re-s off.
ive always been unlocked. for S&Gs,i dumped mmcblk0p3 and found the described "HTCU" at 0x8404. changed it to 0x00000000 and voila! back to locked

afterward,relfashed my origianl mmcblk0p3,wich brought me back to unlocked with no getting or flashing tokens.
this is NOT a patched or hex edited hboot.again,this is ONLY to get back your original ***locked*** status.
*this is for s-off phones only
2 ways to do it:
1)old school
this assumes you to have drivers,adb/fastboot,a hex editor,a fair understanding about what youre doing,and the ability to follow directions on the linked thread
Code:
Microsoft Windows [Version 6.1.7601]
Copyright (c) 2009 Microsoft Corporation. All rights reserved.
C:\Users\Scott>[COLOR="Red"]cd c:\mini-adb_vigor[/COLOR]
c:\mini-adb_vigor>[COLOR="red"]adb devices[/COLOR]
* daemon not running. starting it now *
* daemon started successfully *
List of devices attached
HTxxxxxxxxxx device
c:\mini-adb_vigor>[COLOR="Red"]adb shell[/COLOR]
shell@android:/ $ [COLOR="red"]su[/COLOR]
su
shell@android:/ # [COLOR="red"]dd if=/dev/block/mmcblk0p3 of=/sdcard2/mmcblk0p3[/COLOR]
dd if=/dev/block/mmcblk0p3 of=/sdcard2/mmcblk0p3
64734+0 records in
64734+0 records out
33143808 bytes transferred in 9.519 secs (3481858 bytes/sec)
shell@android:/ # [COLOR="red"]exit[/COLOR]
exit
shell@android:/ $ [COLOR="red"]exit[/COLOR]
exit
c:\mini-adb_vigor>[COLOR="red"]adb pull /sdcard2/mmcblk0p3[/COLOR]
2292 KB/s (33143808 bytes in 14.116s)
[COLOR="Blue"]*modify mmcblk0p3 with a hex editor[/COLOR]
c:\mini-adb_vigor>[COLOR="Red"]adb push mmcblk0p3mod /sdcard2/mmcblk0p3mod[/COLOR]
2478 KB/s (33143808 bytes in 13.059s)
c:\mini-adb_vigor>[COLOR="red"]adb shell[/COLOR]
shell@android:/ $ [COLOR="red"]su[/COLOR]
su
shell@android:/ # [COLOR="red"]dd if=/sdcard2/mmcblk0p3mod of=/dev/block/mmcblk0p3[/COLOR]
dd if=/sdcard2/mmcblk0p3mod of=/dev/block/mmcblk0p3
64734+0 records in
64734+0 records out
33143808 bytes transferred in 18.937 secs (1750214 bytes/sec)
shell@android:/ #[COLOR="red"] exit[/COLOR]
exit
shell@android:/ $ [COLOR="red"]exit[/COLOR]
exit
c:\mini-adb_vigor>[COLOR="red"]adb reboot bootloader[/COLOR]
c:\mini-adb_vigor>2)noob friendly
-download the appropriate zips,place on sd card.
-boot to recoverywipe cache/dalvik
-flash in recovery. i recomend to run query first,to make sure its working. tested on my personal amaze,jetstream,rezound,inc 4g,sensation,MT4GS,and gsm evo 3d.
query:query_bootloader.zip
query_bootloader.zip f335f78f9f46469c823da0c671026de5
unlock:unlock_bootloader.zip
unlock_bootloader.zip f335f78f9f46469c823da0c671026de5
lock:lock_bootloader.zip
lock_bootloader.zip f335f78f9f46469c823da0c671026de5
a little bit of explanation. yes,the md5s are all the same. its the same file,just named differently. the script behaves based on the name of the zip. i knew if i only included 1 download and instructed folks to change the name there would be confusion,so this is my attempt to keep it simple. feel free to download one file and just change the name to make the other zips.
it also works to make your phone relocked if for some reason you want it that way(rename relock_bootloader.zip). i didnt include a zip for that because i figued there would be no demand.
before:

after:

sure,i could have easily faked the above photos,but i dint.

again,all credit goes to s trace on the above thread,be sure to click the thanks button on his post. all i did was remove the device check per his instruction. DO NOT flash on other devices without checking for the proper location of the lock flag first.
DISCLAIMER:this is not my work. i have tested it on my own device,but use it at your own risk. if it melts your phone into a lil pile of goo,its not my fault.
enjoy

special thanks
-brian for unlocking his bootloader,then dumping mmcblock0p3 to make sure it would work for cdma evo3d phones too

-brian and donb for fearless testing of the zip files on evo3d cdma

