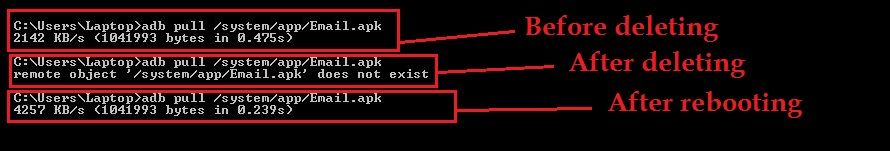
***@**:~$ telnet 192.168.1.144 2222
Trying 192.168.1.144...
Connected to 192.168.1.144.
Escape character is '^]'.
~ $ su
su: must be suid to work properly
~ $ ls
acct init.qcom.class_core.sh persist
cache init.qcom.class_main.sh proc
charger init.qcom.rc res
config init.qcom.ril.path.sh root
d init.qcom.sh sbin
data init.qcom.usb.rc sdcard
default.prop init.qcom.usb.sh storage
dev init.rc sys
etc init.target.rc system
fstab.msm7627a init.trace.rc ueventd.goldfish.rc
init init.usb.rc ueventd.qcom.rc
init.charger.rc logo.bmp ueventd.rc
init.goldfish.rc mnt vendor
~ $ cd /system
/system $ ls
app etc lib tet xbin
bin fonts media usr
build.prop framework partner-app vendor
/system $ exit
Connection closed by foreign host.
***@**:~$ telnet 192.168.1.144 22
Trying 192.168.1.144...
Connected to 192.168.1.144.
Escape character is '^]'.
~ # su
FIX ME! implement ttyname_r() bionic/libc/bionic/stubs.c:466
root@android:/ # mount -o rw,remount /system
root@android:/ # mount
rootfs / rootfs ro,relatime 0 0
tmpfs /dev tmpfs rw,nosuid,relatime,mode=755 0 0
devpts /dev/pts devpts rw,relatime,mode=600 0 0
proc /proc proc rw,relatime 0 0
sysfs /sys sysfs rw,relatime 0 0
none /acct cgroup rw,relatime,cpuacct 0 0
tmpfs /mnt/asec tmpfs rw,relatime,mode=755,gid=1000 0 0
tmpfs /mnt/obb tmpfs rw,relatime,mode=755,gid=1000 0 0
none /dev/cpuctl cgroup rw,relatime,cpu 0 0
/dev/block/mmcblk0p19 /system ext4 rw,relatime,data=ordered 0 0
/dev/block/platform/msm_sdcc.3/by-num/p22 /data ext4 rw,nosuid,nodev,relatime,noauto_da_alloc,data=ordered 0 0
/dev/block/mmcblk0p10 /persist ext4 rw,nosuid,nodev,relatime,data=ordered 0 0
/dev/block/mmcblk0p21 /cache ext4 rw,nosuid,nodev,relatime,data=ordered 0 0
/dev/fuse /storage/sdcard1 fuse rw,nosuid,nodev,relatime,user_id=1023,group_id=1023,default_permissions,allow_other 0 0
/dev/block/vold/179:33 /storage/sdcard0 vfat rw,dirsync,nosuid,nodev,noexec,relatime,uid=1000,gid=1015,fmask=0002,dmask=0002,allow_utime=0020,codepage=cp437,iocharset=iso8859-1,shortname=mixed,utf8,errors=remount-ro 0 0
/dev/block/vold/179:33 /mnt/secure/asec vfat rw,dirsync,nosuid,nodev,noexec,relatime,uid=1000,gid=1015,fmask=0002,dmask=0002,allow_utime=0020,codepage=cp437,iocharset=iso8859-1,shortname=mixed,utf8,errors=remount-ro 0 0
tmpfs /storage/sdcard0/.android_secure tmpfs ro,relatime,size=0k,mode=000 0 0
root@android:/ # cd /system
root@android:/system # ls
app
bin
build.prop
etc
fonts
framework
lib
media
partner-app
tet
usr
vendor
xbin
root@android:/system # echo test >> test.txt
sh: can't create test.txt: I/O error
1|root@android:/system # mount
rootfs / rootfs ro,relatime 0 0
tmpfs /dev tmpfs rw,nosuid,relatime,mode=755 0 0
devpts /dev/pts devpts rw,relatime,mode=600 0 0
proc /proc proc rw,relatime 0 0
sysfs /sys sysfs rw,relatime 0 0
none /acct cgroup rw,relatime,cpuacct 0 0
tmpfs /mnt/asec tmpfs rw,relatime,mode=755,gid=1000 0 0
~ # exit
Connection closed by foreign host.
***@**:~$ clear
***@**:~$ telnet 192.168.1.144 2222
Trying 192.168.1.144...
Connected to 192.168.1.144.
Escape character is '^]'.
~ $ su
su: must be suid to work properly
~ $ cp
BusyBox v1.21.1 (2013-10-18 12:31:34 PDT) multi-call binary.
Usage: cp [OPTIONS] SOURCE... DEST
Copy SOURCE(s) to DEST
-a Same as -dpR
-R,-r Recurse
-d,-P Preserve symlinks (default if -R)
-L Follow all symlinks
-H Follow symlinks on command line
-p Preserve file attributes if possible
-f Overwrite
-i Prompt before overwrite
-l,-s Create (sym)links
~ $ ping 8.8.8.8
PING 8.8.8.8 (8.8.8.8): 56 data bytes
ping: permission denied (are you root?)
~ $ exit
Connection closed by foreign host.
***@**0:~$ telnet 192.168.1.144 22
Trying 192.168.1.144...
Connected to 192.168.1.144.
Escape character is '^]'.
~ # su
FIX ME! implement ttyname_r() bionic/libc/bionic/stubs.c:466
root@android:/ # mount -o rw,remount /system
root@android:/ # mount
rootfs / rootfs ro,relatime 0 0
tmpfs /dev tmpfs rw,nosuid,relatime,mode=755 0 0
devpts /dev/pts devpts rw,relatime,mode=600 0 0
proc /proc proc rw,relatime 0 0
sysfs /sys sysfs rw,relatime 0 0
none /acct cgroup rw,relatime,cpuacct 0 0
tmpfs /mnt/asec tmpfs rw,relatime,mode=755,gid=1000 0 0
tmpfs /mnt/obb tmpfs rw,relatime,mode=755,gid=1000 0 0
none /dev/cpuctl cgroup rw,relatime,cpu 0 0
/dev/block/mmcblk0p19 /system ext4 rw,relatime,data=ordered 0 0
/dev/block/platform/msm_sdcc.3/by-num/p22 /data ext4 rw,nosuid,nodev,relatime,noauto_da_alloc,data=ordered 0 0
/dev/block/mmcblk0p10 /persist ext4 rw,nosuid,nodev,relatime,data=ordered 0 0
/dev/block/mmcblk0p21 /cache ext4 rw,nosuid,nodev,relatime,data=ordered 0 0
/dev/fuse /storage/sdcard1 fuse rw,nosuid,nodev,relatime,user_id=1023,group_id=1023,default_permissions,allow_other 0 0
/dev/block/vold/179:33 /storage/sdcard0 vfat rw,dirsync,nosuid,nodev,noexec,relatime,uid=1000,gid=1015,fmask=0002,dmask=0002,allow_utime=0020,codepage=cp437,iocharset=iso8859-1,shortname=mixed,utf8,errors=remount-ro 0 0
/dev/block/vold/179:33 /mnt/secure/asec vfat rw,dirsync,nosuid,nodev,noexec,relatime,uid=1000,gid=1015,fmask=0002,dmask=0002,allow_utime=0020,codepage=cp437,iocharset=iso8859-1,shortname=mixed,utf8,errors=remount-ro 0 0
tmpfs /storage/sdcard0/.android_secure tmpfs ro,relatime,size=0k,mode=000 0 0
root@android:/ # busybox cp /data/local/tmp/su /system
root@android:/ # busybox cp /system/su xbin
cp: can't create 'xbin': Read-only file system
1|root@android:/ # mount
rootfs / rootfs ro,relatime 0 0
tmpfs /dev tmpfs rw,nosuid,relatime,mode=755 0 0
devpts /dev/pts devpts rw,relatime,mode=600 0 0
proc /proc proc rw,relatime 0 0
sysfs /sys sysfs rw,relatime 0 0
none /acct cgroup rw,relatime,cpuacct 0 0
tmpfs /mnt/asec tmpfs rw,relatime,mode=755,gid=1000 0 0
tmpfs /mnt/obb tmpfs rw,relatime,mode=755,gid=1000 0 0
none /dev/cpuctl cgroup rw,relatime,cpu 0 0
/dev/block/mmcblk0p19 /system ext4 rw,relatime,data=ordered 0 0
/dev/block/platform/msm_sdcc.3/by-num/p22 /data ext4 rw,nosuid,nodev,relatime,noauto_da_alloc,data=ordered 0 0
/dev/block/mmcblk0p10 /persist ext4 rw,nosuid,nodev,relatime,data=ordered 0 0
/dev/block/mmcblk0p21 /cache ext4 rw,nosuid,nodev,relatime,data=ordered 0 0
/dev/fuse /storage/sdcard1 fuse rw,nosuid,nodev,relatime,user_id=1023,group_id=1023,default_permissions,allow_other 0 0
/dev/block/vold/179:33 /storage/sdcard0 vfat rw,dirsync,nosuid,nodev,noexec,relatime,uid=1000,gid=1015,fmask=0002,dmask=0002,allow_utime=0020,codepage=cp437,iocharset=iso8859-1,shortname=mixed,utf8,errors=remount-ro 0 0
/dev/block/vold/179:33 /mnt/secure/asec vfat rw,dirsync,nosuid,nodev,noexec,relatime,uid=1000,gid=1015,fmask=0002,dmask=0002,allow_utime=0020,codepage=cp437,iocharset=iso8859-1,shortname=mixed,utf8,errors=remount-ro 0 0
tmpfs /storage/sdcard0/.android_secure tmpfs ro,relatime,size=0k,mode=000 0 0
root@android:/ # cd /system
root@android:/system # ls
app
bin
build.prop
etc
fonts
framework
lib
media
partner-app
su
tet
usr
vendor
xbin
root@android:/system # rm su
root@android:/system # busybox cp /data/local/tmp/su /system/xbin
root@android:/system # cd xbin
root@android:/system/xbin # ls
dexdump
su
root@android:/system/xbin # busybox chmod 06755 su
root@android:/system/xbin # ls -l
-rwxr-xr-x root shell 55664 2013-07-19 11:20 dexdump
-rwsr-sr-x root root 380532 2014-05-16 22:02 su
root@android:/system/xbin # mount
rootfs / rootfs ro,relatime 0 0
tmpfs /dev tmpfs rw,nosuid,relatime,mode=755 0 0
devpts /dev/pts devpts rw,relatime,mode=600 0 0
proc /proc proc rw,relatime 0 0
sysfs /sys sysfs rw,relatime 0 0
none /acct cgroup rw,relatime,cpuacct 0 0
tmpfs /mnt/asec tmpfs rw,relatime,mode=755,gid=1000 0 0
tmpfs /mnt/obb tmpfs rw,relatime,mode=755,gid=1000 0 0
none /dev/cpuctl cgroup rw,relatime,cpu 0 0
/dev/block/mmcblk0p19 /system ext4 ro,relatime,data=ordered 0 0
/dev/block/platform/msm_sdcc.3/by-num/p22 /data ext4 rw,nosuid,nodev,relatime,noauto_da_alloc,data=ordered 0 0
/dev/block/mmcblk0p10 /persist ext4 rw,nosuid,nodev,relatime,data=ordered 0 0
/dev/block/mmcblk0p21 /cache ext4 rw,nosuid,nodev,relatime,data=ordered 0 0
/dev/fuse /storage/sdcard1 fuse rw,nosuid,nodev,relatime,user_id=1023,group_id=1023,default_permissions,allow_other 0 0
/dev/block/vold/179:33 /storage/sdcard0 vfat rw,dirsync,nosuid,nodev,noexec,relatime,uid=1000,gid=1015,fmask=0002,dmask=0002,allow_utime=0020,codepage=cp437,iocharset=iso8859-1,shortname=mixed,utf8,errors=remount-ro 0 0
/dev/block/vold/179:33 /mnt/secure/asec vfat rw,dirsync,nosuid,nodev,noexec,relatime,uid=1000,gid=1015,fmask=0002,dmask=0002,allow_utime=0020,codepage=cp437,iocharset=iso8859-1,shortname=mixed,utf8,errors=remount-ro 0 0
tmpfs /storage/sdcard0/.android_secure tmpfs ro,relatime,size=0k,mode=000 0 0
root@android:/system/xbin # ls
dexdump
root@android:/system/xbin #
*********** NOTE *************
Right before the last mount command is when i tried giving root access to the Adaway app, but obviously something was screwed up and everything got reverted and /system was mounted read-only again.


 cguru:
cguru: