stayboogy
Android Expert
So as Bugmenot_Rules said, I did, and can, get very, very temporary root access:
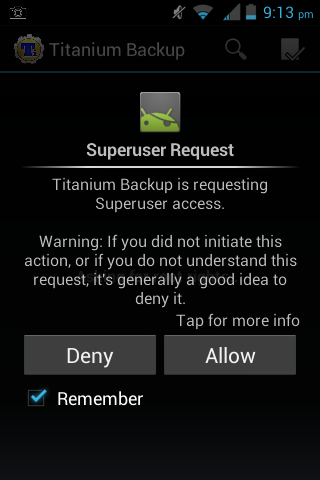
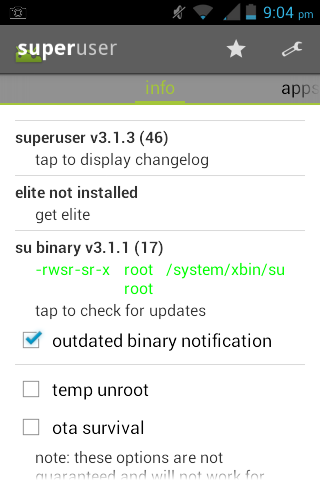
As you can see, it does look like true root. However, it is not even close, even to temp root. Heres the latest why.
After accepting root access once (ex. Titanium Backup) you can use root privileges in that app. If you close and reopen it, or try to use another app, you cannot use root privileges again until you reboot, and run cmds again. The superuser app also recognizes it incorrectly after that, as shown by jjfriede (see this page). It seemes that the firmware is constantly scanning the FS for any sort of SU, as this happens without a reboot.cguru:
The other thing is that when I deleted LiveWallpapers.apk and Email.apk, I thought they hadnt returned for some reason, and thats what I told Bugmenot_Rules. However, I was wrong. I investigated it more recently and yes, they did return:
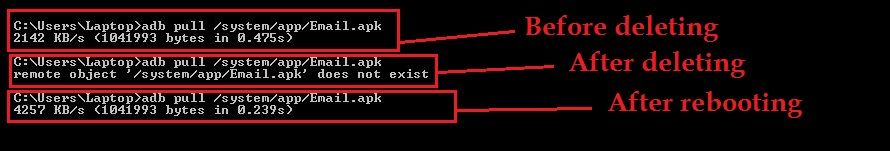
So that means that there IS something replacing the apps on reboot. Whether it is another partition or what, I dont know.
For those that would like to try the method, go here https://github.com/benjimt/RootMyValet/blob/master/Install.txt and follow method 2.
Follow the latest progress here: https://github.com/Unkn0wn0ne/RootMyValet/issues?state=open
thanks for this.
so again, simply and technically, temp root has not really been gained then, as far as system rw access is concerned--just hasn't happened.
i'd like to know what exactly is happening. it's nothing embedded in the ramdisk as far as i can tell. i've been up and down the .rc files and can't find anything of interest to help with these matters.
if we could ever figure out what verifies the boot partition's hash/size, and then modify to accept the new boot with ro.secure=0 then we'd be in business because the boot.img unpacks and packs quite easily and is easily flashed through the telnet exploit


 I've updated the wiki to include the latest method for temp rooting, that partially, and only sometimes works.
I've updated the wiki to include the latest method for temp rooting, that partially, and only sometimes works.