ironass
Extreme Android User
(UPDATE See post #3)
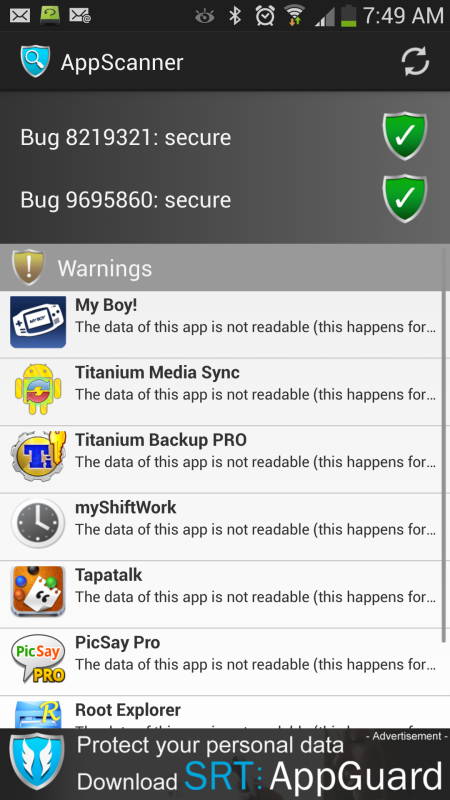
Earlier last month, RFP from BlueBox published a sneak preview of his upcoming BlackHat talk, detailing a vulnerability in the Android platform that affects nearly all Android devices. Soon after, a vulnerability of similar nature and impact was published on Chinese forum. Both of these "Master Key" vulnerabilities allow an attacker to modify the code of an Android package without affecting the signature of the package as verified by the package manager, which has serious implications when considering system-signed packages. From an end user perspective, the vulnerabilities allow an attacker to take full control of a user's device.
Google will be issuing a fix for this in their newer releases of Android firmware. However, these fixes will take time to filter down the food chain from Google to carriers to users... if indeed, a firmware update is even issued for older devices that are now past End of Life, since this vulnerability affects 99% of all Android devices going back to Android 1.6, Donut.
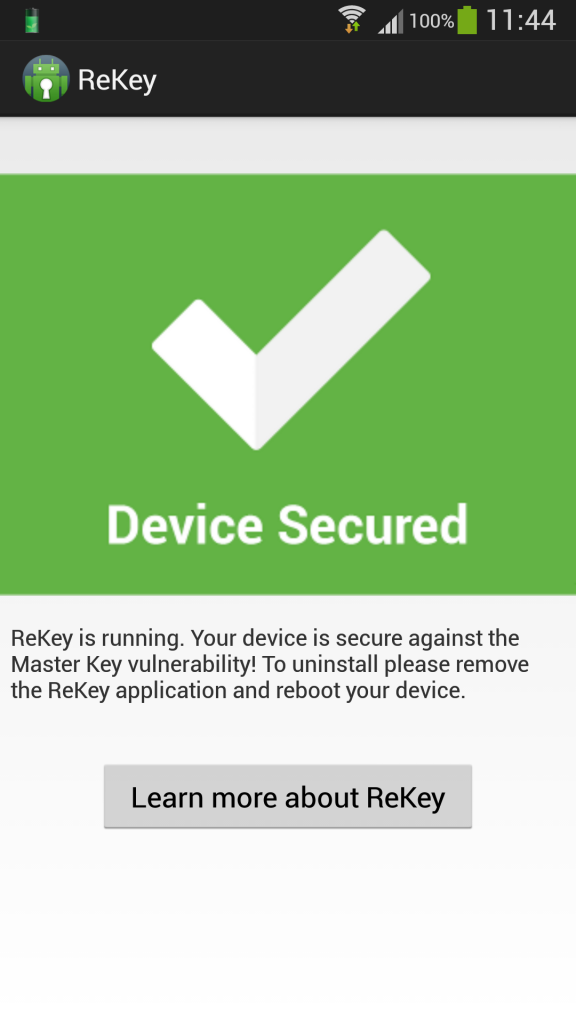
Not wishing to take a chance, I have installed an app, free from the Play Store, which is the result of a research collaboration between Duo Security, a cloud-based two-factor authentication and mobile security company, and Northeastern University's System Security Lab (NEU SecLab) and patches the, "Master Key", vulnerabilities on rooted devices.
The patch is not phone, device or firmware specific... you can whack it on any Android device that is rooted. Once activated it patches the device but should you flash a different firmware you will need to patch it again.
The app is ReKey and can be downloaded from the Play Store
Download
Source
Earlier last month, RFP from BlueBox published a sneak preview of his upcoming BlackHat talk, detailing a vulnerability in the Android platform that affects nearly all Android devices. Soon after, a vulnerability of similar nature and impact was published on Chinese forum. Both of these "Master Key" vulnerabilities allow an attacker to modify the code of an Android package without affecting the signature of the package as verified by the package manager, which has serious implications when considering system-signed packages. From an end user perspective, the vulnerabilities allow an attacker to take full control of a user's device.
Google will be issuing a fix for this in their newer releases of Android firmware. However, these fixes will take time to filter down the food chain from Google to carriers to users... if indeed, a firmware update is even issued for older devices that are now past End of Life, since this vulnerability affects 99% of all Android devices going back to Android 1.6, Donut.
Not wishing to take a chance, I have installed an app, free from the Play Store, which is the result of a research collaboration between Duo Security, a cloud-based two-factor authentication and mobile security company, and Northeastern University's System Security Lab (NEU SecLab) and patches the, "Master Key", vulnerabilities on rooted devices.
The patch is not phone, device or firmware specific... you can whack it on any Android device that is rooted. Once activated it patches the device but should you flash a different firmware you will need to patch it again.
The app is ReKey and can be downloaded from the Play Store
Download
Source


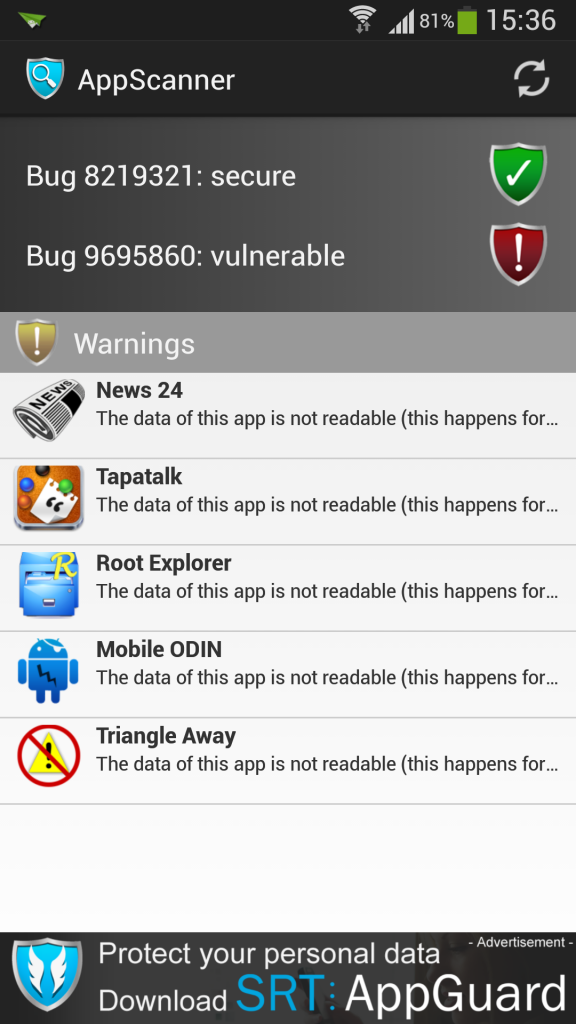
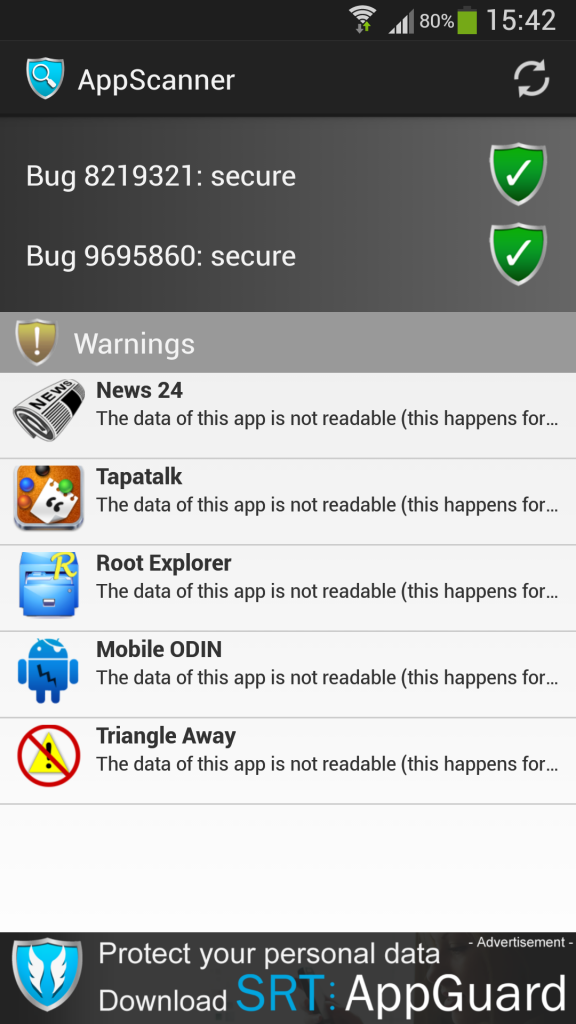
 thanks for clearing that up though
thanks for clearing that up though